authority-to-operate
Blockchain Systems and ATO
Status of this Document
This is a working document of the EEA’s Authority to Operate Working Group, made available for public comment as is, with no implied or express warranty of any kind. It is inappropriate to cite this document except as work in progress. The document may be modified or superseded at any time. This document has not been reviewed or approved by the EEA, its board, or its general membership.
This document is copyright ©2022-2023 EEA Inc. The content of this document can be used under the terms of the Apache 2.0 License.
Introduction
There are many different ways Ethereum blockchain can be leveraged in a system. This has an impact on the ATO process. This section provides insight on which parts of the system may be subject to ATO rules, depending mostly on where relevant data resides inside the system; the following diagrams present three different possible configurations.
Network configurations
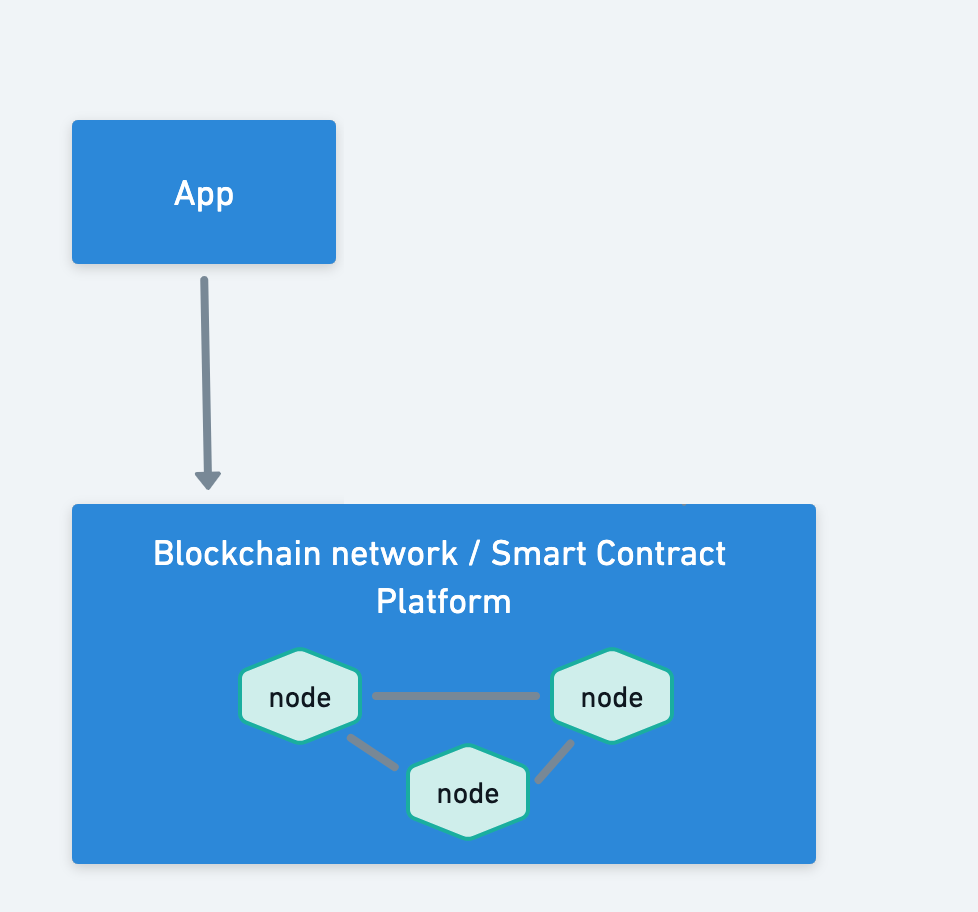
At a high level, a typical way to use a DLT system is to build an application that relies on a DLT / smart contract platform.
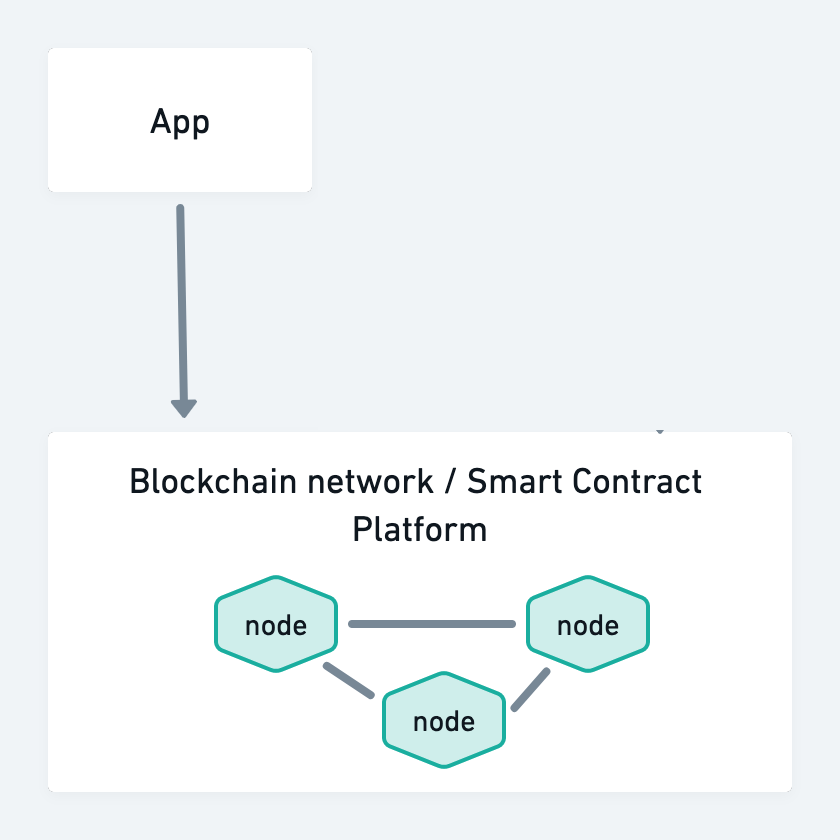
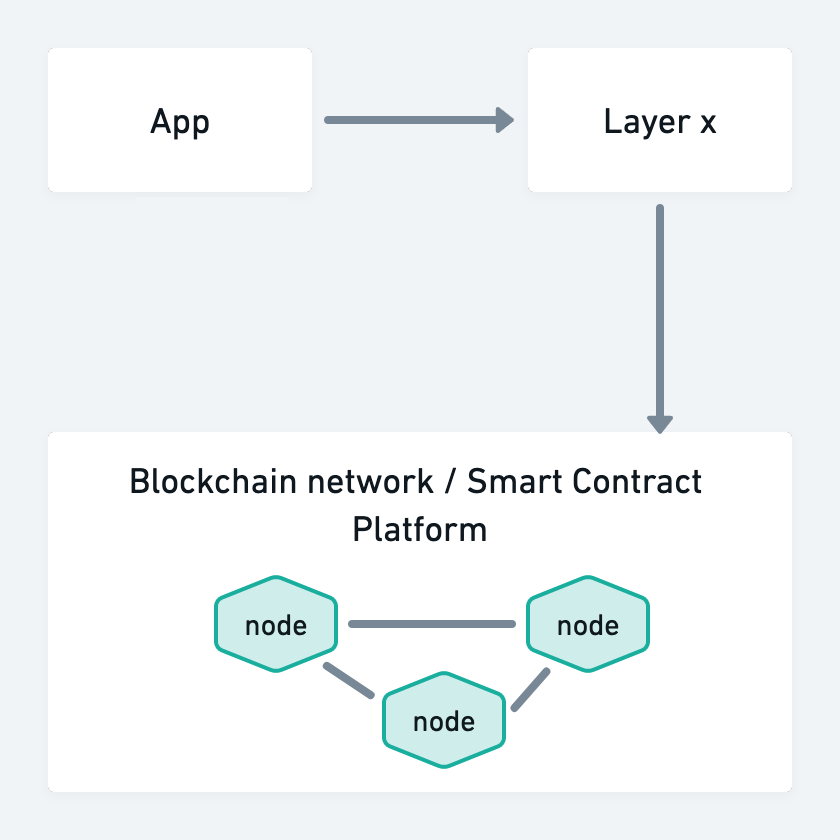
It is also possible to build the app on a Layer 2 system. This layer can itself be a blockchain platform, although its configuration may be different from the underlying blockchain, for example because control is centralized with Proof of Authority consensus. It can also be a different platform, that periodically records its state on the underlying DLT.
The blockchain will usually be distributed amongst different entities that will operate nodes and be responsible for executing tasks such as accepting and processing transactions, proposing new blocks, and validating transactions and blocks.
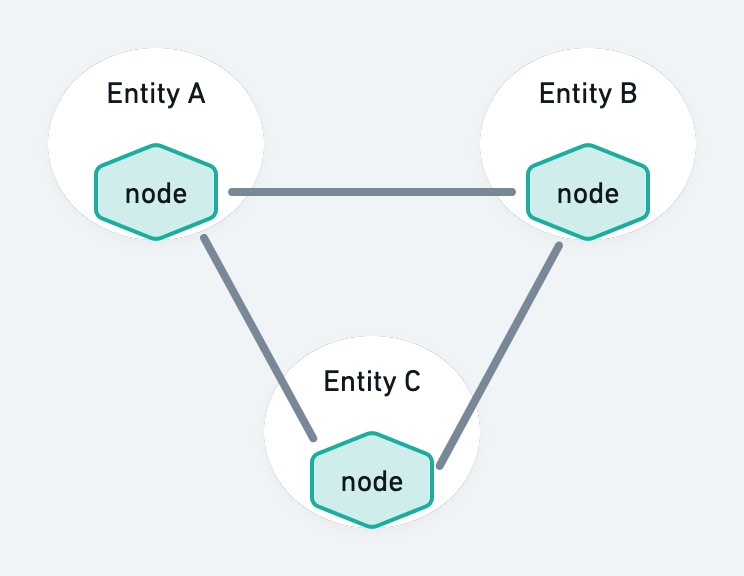
This brings some benefits:
- Data in such a blockchain-based application will be replicated and controlled by these different entities with no need for intermediaries;
- This data will be traceable.
It also brings challenges
- The task of securing the data is now shared amongst the entities involved.
Which parts are relevant for ATO?
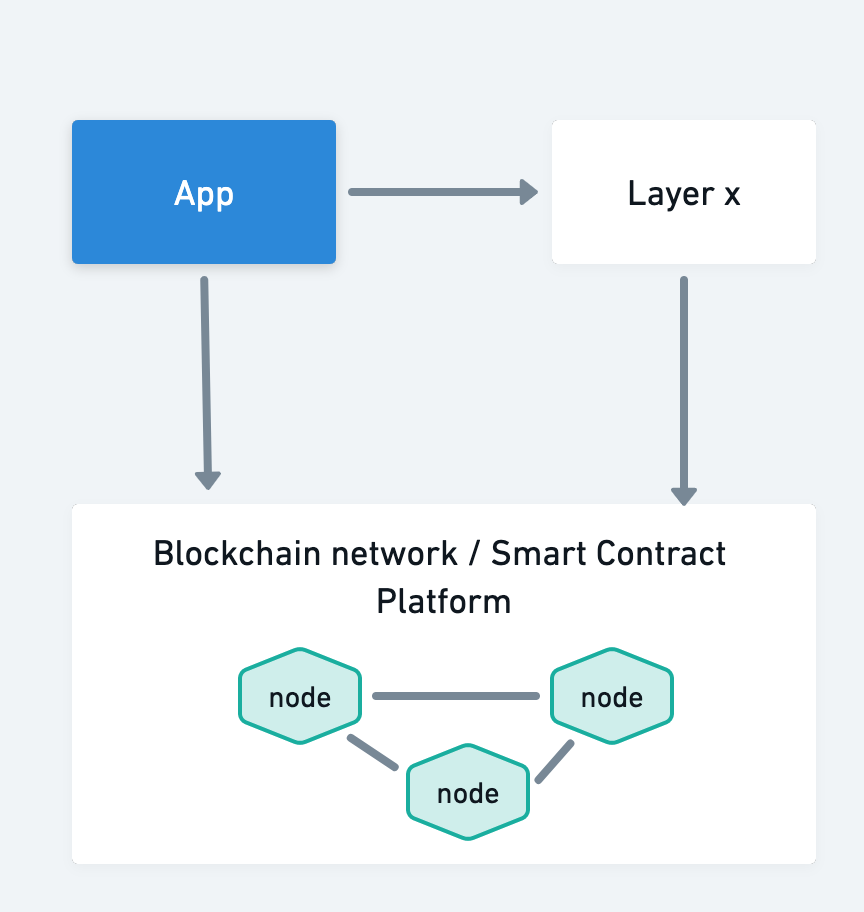
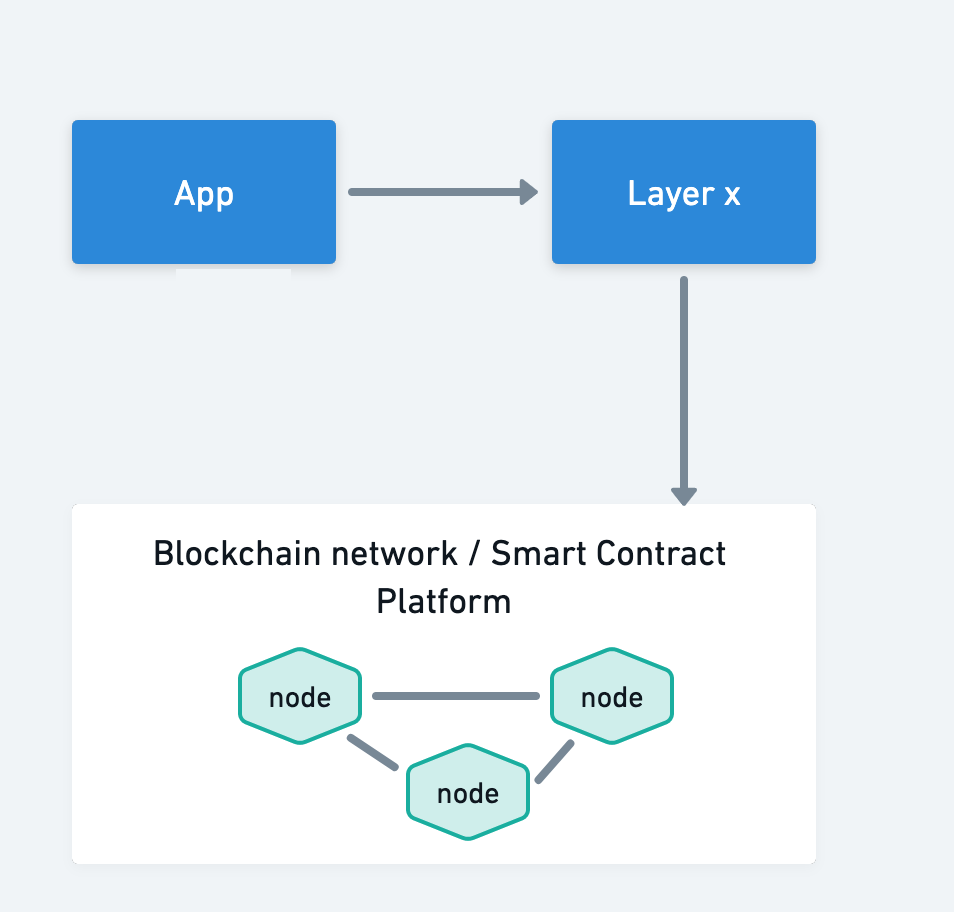
(In the next 3 diagrams, the boxes filled in blue represent components where the relevant data is being handled)
All data in the App
For some use cases, the relevant data is limited to the application component, and not be recorded in the DLT / smart contract platform or intermediary layers. In such cases, whether the App is running on a Layer, or directly on the underlying blockchain, it is only the App that needs Authority to Operate.
Such use cases include applications leveraging trusted oracle data (e.g. Chainlink) that do not leak relevant data to the blockchain or Layer it is operating on.
Data shared with an intermediate layer
For use cases where the relevant data would be handled by one or more intermediary layers as well as the application component, both those Layers and the App itself will need Authority to Operate.
Data shared with the underlying Blockchain
In use cases where the government data would directly be handled by the blockchain platform as well as the application component, whether they use a Layer X approach or not, all the relevant components need Authority to Operate.