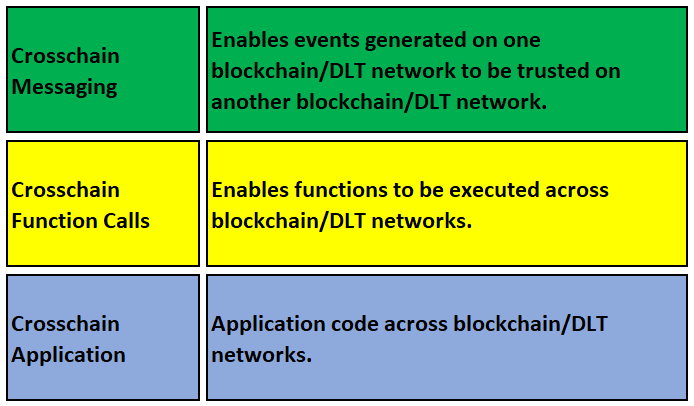
Crosschain Messaging Layer
The Crosschain Messaging layer establishes the peer-to-peer communications infrastructure that enables interoperation between blockchain or DLT networks.
This section describes the required protocols, message formats, and mechanisms for one network to prove the integrity
and authenticity of data to another. This includes specifics around event-based, state-based, and transaction-based
messaging to cater to diverse crosschain information exchange requirements. Additionally, the section covers format
standards for crosschain proofs and considerations for secure transmission of verified data between networks. As several cryptographic approaches are available to afford these protections, the application developer needs to take these options into consideration when developing applications which utilize the crosschain messaging functions.
Crosschain Message Relays
This section describes various mechanisms through which messages are relayed from one blockchain to another, ensuring
that the information can be trusted. This is fundamental to the operation of crosschain functions because the
reliability and security of crosschain operations depend on the integrity of the message relay methods.
Understanding the strengths and weaknesses of various approaches is setting an important context for later understanding
the technical requirements around event-based, state-based, and transaction-based messaging.
- Multisig Relay: a mechanism that leverages multi-signature consensus for relaying messages across blockchains. In this approach, the message originating from a source chain is cryptographically signed by multiple independent relay nodes. These relay nodes or validators have public key signatures that are registered and verified against a whitelist of trusted nodes maintained on the target chain's smart contract. The relay nodes' signatures on the message are aggregated and attached to the communication payload sent from the source chain to the smart contract on the target chain. The target chain's smart contract first verifies that the aggregate signature comprises valid signatures from a threshold number of trusted relayers according to the whitelist. This blockchain-based consensus check establishes multiple attestations of the message's authenticity and integrity. If the multi-signature passes the policy set on the target chain, the message is deemed to have originated genuinely from the source system and can be processed and trusted accordingly by the target chain. By decentralizing the act of relaying through multiple participating validators and embedding multi-signature thresholds on target chains, multisig message relay aims to provide stronger security, availability and integrity assurances for crosschain messaging.
- MPC (Multi-Party Computing) relay: differs from multisig in that it involves only a single relay address affiliated with the relaying activity between networks. This relay address does not have access to the full private key - instead the private key is shared into segments and distributed in a cryptographically secure manner among a set of MPC nodes. These nodes engage in secure multi-party computation protocols to jointly sign messages sent from the relay address without any node revealing its share of the private key. By having at least a threshold of MPC nodes participate in approving the transmission of crosschain messages, the system can replicate the authentication assurances of a valid digital signature without a single privileged entity. The relay address is configured on the target chain and trusted to send messages from the source system. The target chain smart contract does not need to hold a whitelist of trusted relayers as in multisig – rather the relaying participants and business logic are abstracted behind the single relay address governed by decentralized MPC protocols. This approach balances both security as well as efficiency goals for crosschain messaging.
- ZKP (Zero Knowledge Proof) relay: a mechanism that utilizes modern cryptographic proof constructions to validate integrity of crosschain messages without revealing actual content. There are two main approaches - SNARKs (Succinct Non-Interactive Arguments of Knowledge) and STARKs (Scalable Transparent Arguments of Knowledge). In SNARK-based relay, parameters are precomputed among the underlying ZKP system partners to optimize proof generation efficiency. This however necessitates a trusted setup ceremony. In STARK-based relay, the proofs do not rely on any fixed reference string or parameters and hence don't need trusted setup. The ZKP prover computes a proof attesting to authenticity of the crosschain message and transmits this proof to a smart contract on the target chain. The target chain verifies the proof based on its policy to determine if the message originated genuinely from the source system. ZKP relay enhances privacy while enabling target chain participants to still definitively verify integrity of messages. By both eliminating message content exposure as well as third party relayers, it enhances security properties, albeit currently SNARKs pose setup challenges and STARKs have high computation overhead.
- Oracle Relay: An Oracle is a "service that updates a distributed ledger using data from outside of a DLT system" [[ISO22379]]. The ISO Blockchain and Distributed Ledger Technology — Interoperability Framework (ISO/CD TS 23516) categorize oracle interoperability solutions as "Type 1". One possible implementation consists of dedicated Oracle smart contracts deployed on the target chain to handle incoming messages. Oracle nodes run independent off-chain server infrastructure that retrieves data and events from the source system through custom integrations. They collate this external information into standard formats understandable by the oracle contract on the target side. The oracle nodes transmit batched communications to the oracle contracts, which in turn expose APIs for other on-chain smart contracts to access the bridged data. This facilitates target side consumption of verified external data. The model operates through a trust-based federation of oracle nodes which follow expected security practices. By moving the message relaying to dedicated infrastructure operators who stitch source and target chains via custom software, a high degree of flexibility and efficiency is achieved. However lack of decentralization and use of trusted nodes implies some security assumptions for oracle relay versus other peer-to-peer messaging approaches between chains.
- Light Client Relay: a method that involves configuring light clients on the source and target blockchains to enable direct crosschain message transmission leveraging simplified payment verification protocols. In this model, light clients containing current chain headers and consensus rules are instantiated on both sides. The target chain's light client can independently retrieve raw messages from the source system and verify integrity based on header proofs. This allows the target chain to confirm up-to-date state of transactions and events on the source without fully synchronizing the chain or relying on intermediaries. Light client architecture offers low storage requirements and sync times while still providing security inherited from the underlying blockchain.
- Hybrid Relay: a method that method combines multiple crosschain messaging mechanisms to enhance security assurances for bridged communication between chains. It creates two separate relaying pathways for source messages to reach the target chain. For example, the hybrid approach may use an oracle cluster to relay the full message payload with bindings to off-chain anchors and a separate ZKP-based relay to prove cryptographic integrity without revealing contents. The target chain smart contract implements policies checking for payload validity via the oracle channel and proof validation via the ZKP channel. By relaying through multiple modes, adversarial compromisation of any single relay mechanism does not undermine the collective trust assurances. Attackers would need to break both pipelines simultaneously to disrupt message delivery guarantees. While more complex to operate, hybrid relay compensates via defense-in-depth against both infrastructure as well as cryptographic relay attacks. The security benefits exceed standalone relaying, albeit at the expense of more integration effort and technical overhead for bridging systems.
| Setup | Mechanism | Security | Decentralization | Ease of use | Computation | Scalability |
| -------- | ------- | ------- | ------- | ------- | ------- | ------- |
| Multisig | Governance | Aggregation of Signatures | High. Admin addresses safeguarding | Depending on admin nodes. | Easy | Light | High |
| MPC | DKG | Schnorr Signature | Group address safeguarding | Depending on validator nodes. | Easy | Light | High |
| ZKP Snark | Trusted Ceremony | Setup dependent proof key and verfication key | Dependent on secure setup | Medium. More centralized proofer | Difficult | Heavy | Low |
| ZKP Stark | No trusted setup needed | Proof and verification independent of external parameter | High security | Medium. More centralized proofer | Difficult | Heavy | Low |
| Oracle | Collaboration | Smart Contract callback | Trusted Oracle nodes | Medium | Easy | Medium | High |
| Light Client | Weak subjectivity | Header and state verification | High security | No additional trusted actors needed | Medium to Difficult | Medium | High |
| Hybrid method | Dual Channel | Cross checking | Extra security | High | Medium | Medium | Medium |
Crosschain Message Definition
A crosschain message can be categorized, based on the underlying DLT network characteristics, as listed below:
- Event-based: Message payloads are identified with events emitted from the source network.
As an example, an verifiable event can contain the necessary target network specifics and function call data to execute a function on a remote network.
- State-based: Message payloads are identified with source network state updates.
As an example, a verifiable state update, linking back to a specific storage value or account balance via inclusion proofs and state roots, can be used to complete an action on a target network.
- Transaction-based: Message payloads are identified with transactions executed on the source network.
As an example, a verifiable transaction can be translated into a message to be executed on a remote network.
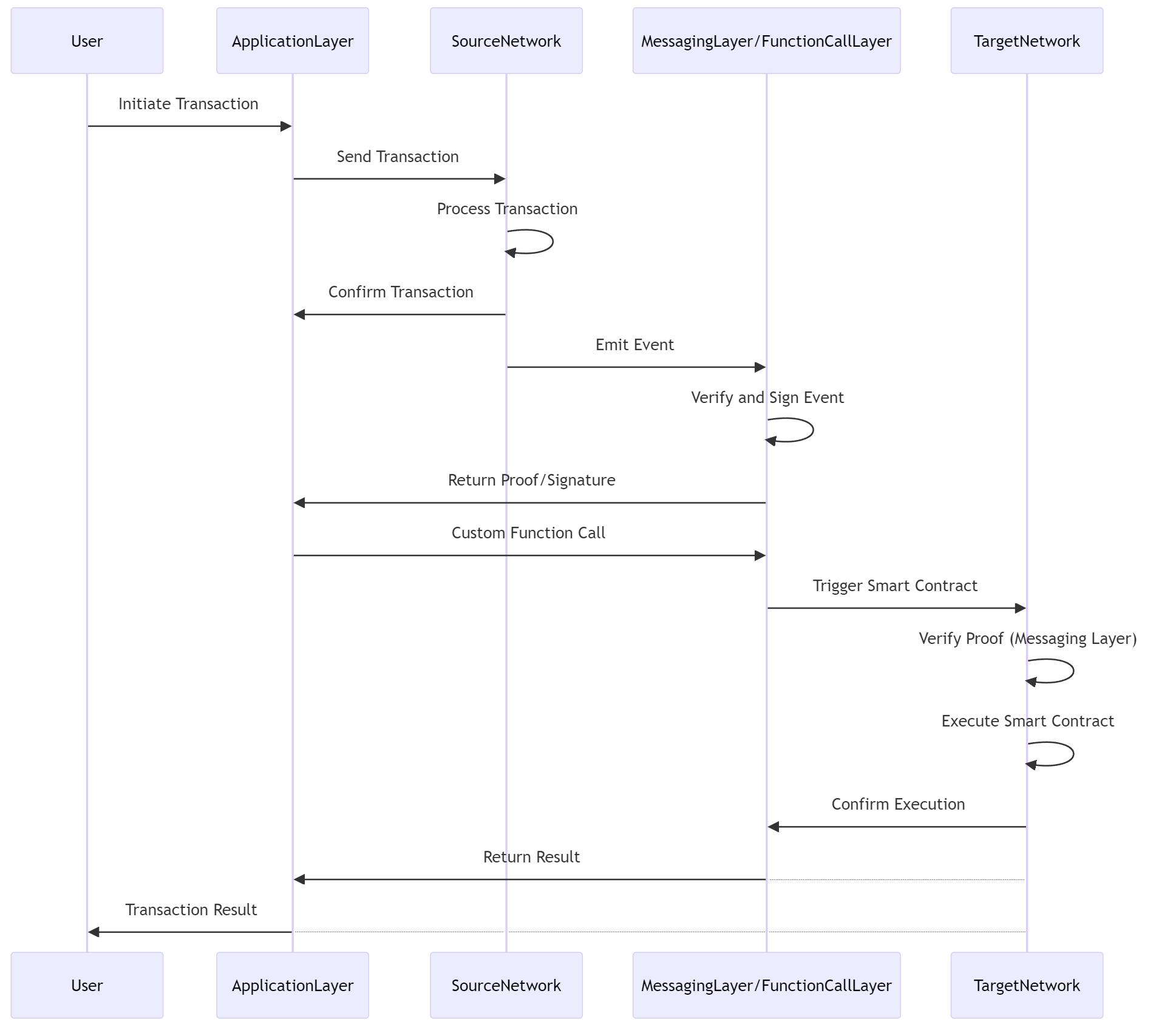
The messaging layer enables secure and standardized communication with diverse DLT networks, allowing messages to be sent and received in a way that supports authentication and verification in a trust-minimized manner. Verification of the event, state change, or transaction becomes synonymous with the verification of the message it contains or is computationally transpiled into.
Crosschain Connector Interface
The crosschain messaging layer is responsible for message authentication and verification. This is achieved by implementing the
ICrosschainConnector interface for a specific network, as outlined in this section. Messaging components that implement the
ICrosschainConnector interface MUST expose public functions equivalent to those defined here.
The decodeAndVerify function takes as inputs the source network identifier, encoded information about the state, transaction,
or event on the source network, and an encoded proof to validate the provided encoded information. This function MAY return
verified information if a valid proof is provided. The function call MUST fail if the proof verification fails. Custom error
codes and messages are RECOMMENDED to provide specific reasons for failure during verification.
The updateAndCommit function takes as inputs the target network identifier, the target contract address (if applicable),
and the function call data to execute on the target network when committing to a crosschain message. This function MAY update
state in the messaging layer or emit an event, depending on the DLT network the connector contract is targeting.
module CrosschainMessaging {
typedef sequence<octet> address;
typedef sequence<octet> uint256;
typedef sequence<octet> bytes;
interface ICrosschainConnector {
void decodeAndVerify(
in uint256 networkId,
in bytes encodedInfo,
in bytes encodedProof,
out bytes decodedInfo
);
void updateAndCommit(
in uint256 networkId,
in address contractAddress,
in bytes functionCallData
);
};
};
The function decodeAndVerify is used to decode and verify message information originating from different networks.
Parameters:
networkId (required): Identification of the source network where the message originated. This can be used to determine the applicable verification scheme.encodedInfo (required): Encoded message containing event, state or transaction data that needs to be decoded and verified according to the network and message category.
encodedProof (required): Encoded proof information and/or signatures that an implementation can use to verify the information given in encodedInfo. The sections below detail the possible formats of this value.
Returns:
decodedInfo: The decoding scheme specific data as decoded from encodedInfo and attested to by encodedProof.
The function (optionally) returns decoded information. To improve efficiency and to avoid another smart contract call
to a connector contract implementation that performs network specific decoding of event data.
If the verification fails for any reason, a revert must prevent any state changes from occurring.
Some example failure cases, requiring a transaction revert, include:
- Decoding failures: The encoded information or encoded proof failed to decode as expected.
- Validation failures: Connector specific validation checks on decoded data failed.
- Verification failure: Provided cryptographic proof is not valid.
By reverting on failed verification, the system ensures data integrity and prevents invalid data from being processed.
The function updateAndCommit is used to make any updates on the local network before commiting to
an outgoing message to a specific target network.
Parameters:
networkId (required): Identification of the target network where the message should be executed.
This can be used to determine the applicable state update or event that needs to be emitted.contractAddress (optional): The address of the contract where the message should be executed on
the target network. Only applicable if the target network makes use of smart contracts.
functionCallData (required): The message content containing the function call data with which
the function should be executed on the target network.
Event-based Messaging Mechanism
Event attestation allows a target network to trust that a event was emitted on a source network, at a specific block
or point in time, after verifying a cryptographic proof attesting to the occurrence of the event.
EVM-based networks natively support event attestation by using the block header's receipt root to prove that events
occurred within a specific block. The receipt root acts as a cryptographic commitment to the list of transaction
receipts, which contain the smart contract event logs.
Alternatively, event attestation can rely on one or more trusted parties signing the event data,
thereby confirming that it occurred on a particular network.
The event data typically includes enough information to trigger an action on the target network after successful verification.
Connector contract implementations can facilitate executable crosschain messages by using the standardized
CrosschainFunctionCall event provided here, or by defining an equivalent event.
module CrosschainMessaging {
typedef sequence<octet> address;
typedef sequence<octet> uint256;
typedef sequence<octet> bytes;
interface ICrosschainConnector {
oneway void CrosschainFunctionCall(
in uint256 networkId,
in address contractAddress,
in bytes functionCallData
);
};
};
The CrosschainFunctionCall event represents a verifiable event on a source network, which can be used
to execute remote function calls on a target network after successful verification.
Properties:
networkId (required): Identification of the target network where the message should be executed.contractAddress (optional): The address of the contract where the message should be executed on the target network. Only applicable if the target network makes use of smart contracts.
functionCallData (required): The function call data with which the message should be executed on the target network.
Event-based Verification
EVM-based networks natively provide a way to verify that an event has been emitted on the source network. A receipt
root is included in each block header and used when verifying a specific event log.
Analog verification schemes exist for non-EVM networks that support verifiable event logs.
Event-based verification is used by interoperable smart contracts on the target network, to verify the validity
and authenticity of the event before using it to execute a corresponding operation locally. The connector contract is used to decode and verify a proof
around the event ensuring that only verified events from the source network can trigger actions on the destination network.
Event-based Interface
The ICrosschainConnector interface defined in Section 3.3, for event-based implementations, are described in this section.
Parameters for decodeAndVerify:
networkId (required): Identification of the source network that emitted the event. This can be
used to determine the verification scheme, to enforce EIP formats for EVMs.
encodedInfo (required): Encoded event information consisting of
the local network identifier (networkId),
the local contract address (contractAddress) and
the remote event data (eventData) to be verified.
encodedProof (required): Encoded proof information and/or signatures that an implementation
can use to verify the information given in as eventData. The format of this proof are outlined in Section 3.7.
Returns:
decodedInfo: The decoding scheme specific data as decoded from encodedInfo. This
can include any information that can be derived from the verified eventData. Eg, returning the
event content as message payload, or extracted execution parameters for local execution, or other verified
results more specific to the local verifying network.
State-based Messaging Mechanism
State attestation allows a target network to trust a source network's state, at a specific block or point in time,
after verifying a cryptographic proof attesting to that state.
For EVM-based networks, state-based messaging relies on the state root in block headers to prove the current state
of the source network. By conveying state roots for particular blocks alongside expected state data encodings,
the destination network can verify specific account balances, contract variables, or other on-chain data stored in the
source network's state tree.
For networks using ZKPs, state updates can be attested through computationally verifiable proofs validating
changes to the network state. The ZKP prover can succinctly demonstrate a particular account balance or contract
storage value transitioned to an expected amount from a previously verified state, while keeping state data opaque.
State-based Verification
Block header proofs for state-based messaging can be used in exactly the same manner as in event-based messaging but
unlike events in transaction receipts, the current header includes states in the past. ZKP circuit specific contracts
can be used for verification of state changes for ZKP capable source networks.
State-based Interface
The ICrosschainConnector interface defined in Section 3.3, for state-based implementations, are described in this section.
Parameters for decodeAndVerify:
networkId (required): Identification of the source network where state was updated. This can be
used to determine the applicable verification scheme.
encodedInfo (required): Encoding of
the local network identifier (networkId),
the local contract address (contractAddress) and
the remote storage root as key-value state data (stateData) to be verified.
encodedProof (required): Encoded proof information and/or signatures that an implementation can use to verify the information given in stateData.
Returns:
decodedInfo: The decoding scheme specific data as decoded from encodedInfo. This can include any information that can be derived from the verified stateData.
Transaction-based Messaging Mechanism
Transaction attestation allows a target network to trust that a transaction was executed on a source network,
at a specific block or point in time, after verifying a cryptographic proof attesting to that transaction.
Transaction-based crosschain messaging relies on conveying transaction information that can be used to prove that
a transaction was executed on the source network. For EVM-based networks, the transaction root in block
headers provides a cryptographic hash structure encapsulating all transactions included within the block. By
transmitting block headers containing a desired transaction hash alongside a Merkle proof tying the transaction
hash to the overall transaction root, the destination network can reliably verify the occurrence of the specific
transaction on the source network.
More broadly, any network that utilizes Merkle trees or similar structures to efficiently store and verify
transactions, can be used in the crosschain messaging protocol to attest that transactions were executed in the network.
Transaction-based Verification
Block header proofs for transaction-based messaging can be used in exactly the same manner as in event-based messaging
by making use of the transaction root. Moreover, a transaction executed in a source network, that is not EVM-based, can
be wrapped in the same way with a Merkle inclusion proof or a ZKP depending on the capabilities of the source network.
Transaction-based Interface
The ICrosschainConnector interface defined in Section 3.3, for transaction-based implementations, are described in this section.
Parameters for decodeAndVerify:
networkId (required): Identification of the source network where the transaction occurred. This can be used to determine the verification scheme.encodedInfo (required): Packed ABI-encoding of
the local network identifier (networkId),
the local contract address (contractAddress)
the remote transaction data (txData) to be verified.
encodedProof (required): ABI-encoded proof information and/or signatures that an implementation can use to verify the information given in txData. The sections below detail the format of this value.
Returns:
decodedInfo: The decoding scheme specific data as decoded from encodedInfo. This can contain the verified local network identifier, contract address and function call data as decoded and interpreted from the given verifiable txData, if the next action to be taken is a remote function call.
Format of proofs
The sections below detail the requirements for the format of proofs.
All event-, transaction- or state-based messaging protocols
MUST support at least one of the following proving schemes:
- Multiple ECDSA (Elliptic Curve Digital Signature Algorithm) Signatures
- Multiple EDDSA (Edwards-curve Digital Signature Algorithm) Signatures
- Multiple Schnorr Signatures
- Multiple BLS Signatures
- Ethereum Block Header Proofs
- Multivalued Merkle Inclusion Proofs
- Zero-knowledge Proofs
For implementations supporting a specific proving scheme, encodedProof MUST contain the Proof struct as defined in this section.
module CrosschainMessaging {
typedef sequence<octet> bytes;
typedef sequence<octet> uint256;
interface ICrosschainConnector {
struct Signature {
bytes by;
uint256 sigR;
uint256 sigS;
uint256 sigV;
bytes meta;
};
struct Proof {
uint256 type;
bytes proofData;
sequence<Signature> signatures;
};
};
};
Definitions:
type: A 256-bit integer to identify the type of proof.proofData: Specialized data required by the proving scheme as a sequence of bytes.signatures: An array of digital signatures if required by the proving scheme.
Notes:
- The contents of
signatures may vary depending on the proving scheme. It is advised to use the type to determine the correct decoding scheme and utilize the meta inside each signature for an array of heterogeneous signatures.
- The
signatures array should only contain signatures for unique by values.
- Some fields will not be applicable, depending on the proving scheme. Use
null or its equivalent in this such a scenario.
Multiple ECDSA Signatures
For implementations supporting multiple ECDSA signatures, Proof MUST contain an array of ECDSA signatures, with each signature tied to a unique signer address or public key.
Definitions:
by: The 160-bit Ethereum address derived from the 257-bit ECDSA public key, or the public key itself.sigR: The ECDSA signature's 256-bit R value.sigS: The ECDSA signature's 256-bit S value.sigV: The ECDSA signature's 8-bit V value containing a recovery byte to be used with the provided by value.meta: The ECDSA signature's metadata containing optional information on the platform, curve and hash function that was used to create the signature.type: The type of proof indicating that the proof contains multiple ECDSA signatures.proofData: Not applicable for this scheme.signatures: An array of ECDSA signatures.
Multiple EDDSA Signatures
For implementations supporting multiple EDDSA signatures, Proof MUST contain an array of EDDSA signatures, with each signature tied to a unique public key.
Definitions:
by: The 256-bit EDDSA public key of the signer.sigR: The EDDSA signature's 256-bit R value.sigS: The EDDSA signature's 256-bit S value.sigV: Not applicable for EDDSA signatures.meta: The EDDSA signature's metadata containing optional information on the platform, curve and hash function that was used to create the signature.type: The type of proof indicating that the proof contains multiple EDDSA signatures.proofData: Not applicable for this scheme.signatures: An array of EDDSA signatures.
Multiple Schnorr Signatures
For implementations supporting multiple Schnorr signatures, Proof MUST contain an array of Schnorr signatures with metadata, with each signature tied to a unique signer public key.
Definitions:
by: The 257-bit compressed Schnorr public key of the signer.sigR: The Schnorr signature's 256-bit R value containing a compressed elliptic point representation.sigS: The Schnorr signature's 256-bit S scalar value.sigV: The Schnorr signature's 8-bit V value containing a recovery byte to be used when decompressing the point R.meta: The Schnorr signature's metadata containing optional information on the platform, curve and hash function that was used to create the signature.typ: The type of proof indicating that the proof contains multiple Schnorr signatures.proofData: Not applicable for this scheme.signatures: An array of Schnorr signatures.
Multiple BLS Signatures
For implementations supporting multiple BLS signatures, encodedProof MUST contain an array of BLS signatures with metadata, with each signature tied to a unique signer public key.
The encodedProof value for a scenario requiring one or more BLS12-381 signatures has the format described in this section.
It contains the ABI-encoded Proof struct as defined above.
Definitions:
by: The 384-bit compressed BLS public key of the signer.sigR: The first 256-bits of the 96 bytes BLS signature.sigS: The second 256-bits of the 96-byte BLS signature.sigV: The third 256-bits of the 96-bytes BLS signature.meta: The BLS signature's metadata containing optional information on the platform, curve and hash function that was used to create the signature.typ: The type of proof indicating that the proof contains multiple BLS signatures.proofData: Not applicable for this scheme.signatures: An array of BLS signatures.
Ethereum Block Header Proofs
For implementations supporting Ethereum block header proofs, encodedProof MUST contain Merkle Patricia proof data and an array of Ethereum validator signatures.
The encodedProof value for a scenario, requiring a Merkle Patricia proof and one or more validator
signatures, has the format described in this section. It contains the ABI-encoded Proof struct as defined below.
module CrosschainMessaging {
typedef sequence<octet> bytes32;
typedef sequence<octet> bytes;
interface CrosschainConnector : ICrosschainConnector {
struct ProofData {
bytes witnesses;
bytes32 root;
bytes32 blockHash;
bytes blockHeaderMeta;
};
};
};
Definitions:
witnesses: The rlp-encoded sibling nodes as witnesses.root: The block receipt, transaction or state root.blockHash: The block hash.blockHeaderMeta: The rlp-encoded Ethereum, or EVM equivalent, block header metadata.by: The 160-bit Ethereum address of the signer.sigR: The ECDSA signature's 256-bit R value.sigS: The ECDSA signature's 256-bit S value.sigV: The ECDSA signature's 8-bit V value.meta: The ECDSA signature's metadata containing optional information on the platform, curve and hashing function that was used to create the signature.typ: The type of proof indicating that the proof contains Ethereum, or EVM equivalent, block header data.proofData: The encoded proof data. The data contained in the proof, e.g. sibling nodes, receipt root, block hash and block headers.signatures: The array of Ethereum validator signatures or equivalent consensus participant signatures.
Multivalued Merkle Inclusion Proofs
For implementations supporting multivalued Merkle inclusion proofs, encodedProof MUST contain a multivalued Merkle proof and an array of, possibly heterogeneous, protocol participant signatures.
The encodedProof value for a scenario, requiring a multivalued Merkle proof and one or more heterogeneous participant signatures, has the format described in this section. It contains the encoded Proof structure as defined below.
module CrosschainMessaging {
interface CrosschainConnector : ICrosschainConnector {
typedef sequence<octet> bytes32;
struct ProofData {
bytes32 root;
sequence<bytes32> witnesses;
sequence<uint8> flags;
sequence<bytes32> values;
}
};
};
Definitions:
root: The Merkle tree root.witnesses: The multivalued Merkle proof's witnesses as an array of 32-byte values.flags: The multivalued Merkle proof's flags as an array of 8-bit unsigned integers.values: The multivalued Merkle proof's leaves as an array of 32-byte values.by: The 256-bit ECDSA public key coordinate or the 256-bit ED25519 public key of the signer.sigR: The ECDSA/EDDSA signature's 256-bit R value.sigS: The ECDSA/EDDSA signature's 256-bit S value.sigV: The ECDSA signature's 8-bit V value.meta: The ECDSA/EDDSA signature's metadata, containing optional information on the platform, curve and hashing function that was used to create the signature.typ: The type of proof indicating that the proof contains multivalued Merkle proof data.proofData: The data contained in the proof, e.g. witnesses, flags, values and a root.signatures: The array of consensus participant signatures.
Zero-knowledge Proofs
For implementations supporting zero-knowledge proofs, encodedProof MUST contain the data points required for the zero-knowledge circuit being used.
The encodedProof value for a scenario requiring a zero-knowledge proof has the format described in this section. It contains the encoded Proof struct as defined below, including elliptic curve pairing points required for the particular zero-knowledge circuit implementation.
module CrosschainMessaging {
interface CrosschainConnector : ICrosschainConnector {
typedef sequence<octet> bytes32;
typedef sequence<octet> uint256;
struct ProofData {
uint256 a[2];
uint256 b[2];
uint256 c[2];
bytes32 meta;
};
};
};
Definitions:
a: First elliptic curve pairing point for zero-knowledge circuit implementation.b: Second elliptic curve pairing point for zero-knowledge circuit implementation.c: Third elliptic curve pairing point for zero-knowledge circuit implementation.meta: The public parameters, such as protocol name, base points and so on.typ: The type of proof indicating that the proof contains zero-knowledge proof data.proofData: The data contained in the proof, e.g. elliptic curve pairing points for a zero-knowledge circuit.signatures: Not applicable for this scheme.
Authentication Parameters
Remote function call components need to determine the source network and contract address that initiated the remote function call. Functions in contracts on destination networks use this information to determine if the caller is authorised to execute the function remotely. The authentication parameters are provided as hidden parameters, that exist outside the scope of the declared function parameters.
Authentication parameters are appended to the call data of a function by the messaging layer, using the applicable crosschain connector for a specific target network. Authentication parameters can similarly be extracted by the messaging layer, using the applicable crosschain connector for a specific source network, to authenticate a message in the function call or application layer.
Compatible crosschain implementations MUST append the hidden authentication parameters to the function call data for authentication on the target network.
Compatible crosschain implementations MUST decode the hidden authentication parameters and authenticate callers for a given source network.
The crosschain connector interface exposes the function encodeAuthParams to append authentication parameters to the function selector and parameter data, and the function decodeAuthParams to extract authenticated parameters from the function call data.
module CrosschainMessaging {
typedef sequence<octet> address;
typedef sequence<octet> uint256;
typedef sequence<octet> bytes;
interface ICrosschainConnector {
void encodeAuthParams(
in bytes functionCallData,
in uint256 networkId,
in address callerAddress,
out bytes augmentedCallData
);
void decodeAuthParams(
in bytes functionCallData,
out uint256 networkId,
out address callerAddress
);
};
}
Where the ICrosschainConnector functions are defined as:
encodeAuthParams: Function used to append the hidden authentication parameters to the function call data, before commiting to the remote function call by means of emitting an event or otherwise.decodeAuthParams: Function used to decode the hidden authentication parameters and authenticate against known inbound callers, for a given source network, before the remote function call can be executed on the remote network.
Where encodeAuthParams parameters are defined as:
functionCallData: The function call data that consists of the encoded function selector and input parameter data with which the remote function should be called.networkId: The identifier of the local network that is committing to the remote function call to be made on the target network.callerAddress: Address of the authenticated sender/contract, or equivalent, on the local network that is authenticated to initiate a call to the remote target network.augmentedCallData: Resulting function call data, where the hidden authentication parameters are appended at the back.
Where decodeAuthParams parameters are defined as:
functionCallData: The function call data that consists of the encoded function selector, input parameter data and hidden authentication parameters.networkId: The decoded/authenticated source network identifier where the remote function call initiated, or its equivalent.callerAddress: The decoded/authenticated caller address that initiated the call on the remote source network, or its equivalent.
Authentication parameters are network specific and the crosschain connector implementation, in the messaging layer, needs to handle them based on the network it is connecting to. The interface provided in this section allows for implementations where the messaging layer does authentication when invoked, and implementations where the function call layer does authentication by using the messaging layer functions only to encode and decode the authentication parameters.
Crosschain Transaction Fees
When messages are relayed across networks, certain crosschain messaging models entail associated fees. In
event-based transfers validated by third-party relayers, the relayers may charge a service fee plus cover gas
costs for submitting proofs on destination chains. To enable transparency, a EstimateFee function can be exposed
to return expected messaging fees based on payload details. It can accept parameters like the target network ID
and estimated gas limit for proof verification. Using these inputs, it can calculate total fees comprising:
-
Relayer service fees based on aspects like message size, relay paradox time, privacy techniques.
-
Gas fees charged on target network for executing transaction verifying the proof submission. Estimated using
expected gas costs given payload complexity and configured gas limit.
The estimated fees returned can inform source network applications on complete crosschain messaging costs
denominated in the payload asset. Upon successful relaying, fees are paid to the relaying contract and distributed
to participating relayers minus gas expenses. For non-relayed state-based transfers where users directly submit
proofs, the function can return just the target network gas estimation required for proof verification. Enabling
fee transparency and estimation guides rational messaging behavior across networks.
For messaging models, that require fees, components MUST support the estimateGas interface function.
module CrosschainMessaging {
interface ICrosschainConnector {
typedef sequence<octet> uint256;
typedef sequence<octet> bytes;
void estimateGas(
in uint256 networkId,
in uint256 gasLimit,
in bytes functionCallData,
out uint256 gasFee
);
};
};
Where estimateGas parameters are defined as:
networkId: The destination network identification.gasLimit: The Ethereum gasLimit, set for the transaction, or its EVM equivalent.functionCallData: The encoded Ethereum smart contract function call data, or its equivalent.gasFee: The estimated Ethereum gas fee, or its equivalent.
Crosschain Messaging Considerations
Levels of Finality
Settlement Finality:
Settlement finality refers to the point at which a transaction is considered complete and irreversible by the system. Once a transaction achieves finality, it cannot be altered, undone, or disputed. This is a critical requirement for many financial and legal applications where certainty about the status of a transaction is necessary.
Probabilistic Finality:
Probabilistic finality means that transactions become increasingly irreversible as more blocks are added to the chain after the block containing the transaction. The security of a transaction is based on the probability that it would be too computationally expensive for an attacker to change the transaction, as they would need to redo the work of the block containing the transaction and all subsequent blocks. Probabilistic finality usually occurs in DLTs that use consensus mechanisms with potential forks, like proof-of-work blockchains.
In industries heavily regulated and requiring clear audit trails (like finance and law), settlement finality is often a legal requirement. Systems operating in these domains must ensure their technology can meet these regulatory standards, making probabilistic finality unsuitable.
In addition, for DLT systems that interact with traditional banking systems or other blockchains, having clear settlement finality can simplify the process of reconciling transactions across different systems, which might have different rules regarding transaction finality.
Level of finality for public permissionless networks.
Implementations must carefully navigate the unique characteristics of the DLT networks on which they operate, ensuring that messages and transactions maintain their integrity and legal standing as they traverse across different ledger systems, and must account for the potential variations in the time to finality and the economic implications of the consensus mechanisms.
For instance, in the context of public permissionless networks utilizing Proof of Stake (PoS) for consensus, such as Ethereum post-Merge, the network offers a form of deterministic finality through mechanisms like the Casper Finality Gadget, where transactions are considered final and irreversible after a certain number of confirmations, backed by economic stakes of validators. This ensures that transactions cannot be reversed without significant financial penalties, providing a stronger assurance of finality compared to probabilistic finality seen in proof-of-work systems.
Level of finality for permissioned networks.
In permissioned networks with consensus mechanisms like proof of authority, immediate deterministic finality can be assumed for chain transactions with sufficient validator signatures. Byzantine fault tolerance provides strong cryptographic guarantees against block reversions. Thus, messaging finality can directly track on-chain settlement without probabilistic relaxations on permissioned environments using consensus algorithms with instant finality. Deferred effects should only be needed in cases of detected validation failures, not due to probabilistic uncertainties.
Consideration of Intent based interoperability
As discussed in the crosschain bridge needs to wait for blocks in both the source chain and the target chain to be finalized in order to complete a crosschain transaction. The wait time impacts the usability of crosschain applications that transfer values from one blockchain to another. Intent-based Crosschain Mechanisms are intended to mitigate the delays.
An Intent-based Mechanism allows a user to submit a request for cross network transfer without the need for specifying which agent and path will carry out the transfer. The Intent Relayer watches for the transfer request in the source chain. Once the source fund is locked by a smart contract, the Intent Relayer registers the crosschain service and deposits the required liquidity on the target chain. The Intent Relayers take a small risk that the source chain may rollback, so their funds deposited on the target chain may not be compensated. Once the source chain transaction is finalized, the Intent Smart Contract pays the funds disbursed, plus a service fee, to the Intent Relayer.
The Intent-based Mechanism can be built on the application layer using the crosschain messaging and execution protocol defined in this specification. The intent Smart Contract on the source chain and the deposit smart contract on the target chain can leverage the messaging layer protocol and register Intent Relayers to the smart contract. Once finality is reached on both chains, the Intent Smart Contract pays the source fund to the Intent Relayers.
Public Key / Address Validation
Some crosschain messaging techniques rely on cryptographic signatures to attest to the validity of data sourced
from external networks. Destination networks will typically maintain a list of authorized public keys alongside
verification rules in their verifier contracts. These contracts will also govern permissions to add or remove
trusted keys from the whitelist based on the sender's address.
For ECDSA signatures, verifier contracts may opt to rather store Ethereum addresses, serving as proxies for actual
public keys, to be used later in verifying signed payloads. Before registering their signing address, participants must
validate possession of the associated private key for signing messages, usually via an eth_sign or EIP-191 personal_sign
operation.
Failing to properly validate the signing identity can bind an invalid address incapable of producing signatures to
manage the registrant’s listing. This prevents erroneously registered entities from later participating in their own removal
or updating their registered signing keys.
Careful key management ensures signature-based messaging can flexibly propagate while preventing spam and manipulation.
Consideration of ZKP as a messaging mechanism
ZK-SNARKs are succinct non-interactive arguments of knowledge that enable privacy-preserving proofs of computation
and integrity. They are well-suited for crosschain messaging due to their short, efficiently verifiable proofs.
ZKP relayers are operators that generate proofs to attest to the validity of messages without revealing the content.
They undergo upfront ceremonies to securely generate proving and verification keys to facilitating subsequent proof
generation workflows. The verification keys are published or configured in smart contracts on the destination network
in order to verify computational proofs attesting to the authenticity of ZKP-encoded messages coming from the source
network.
For crosschain messaging, ZKP relayers follow bi-directional multi-party computation protocols to jointly compute
proofs of events, transactions or state transitions on source networks without leaking raw data. Source network
integrity assertions are encoded into the generated proofs and transmitted to ZK verifier contracts on destination
networks for verification against the published verification keys.
Destination networks can host ZK verifier contracts supporting different proof circuits for multiple types of
ZKP-attested crosschain messages such as asset transfers, trade settlements, identity credentials, etc. By configuring
circuit-specific verifier contracts and relayers with aligned circuits, advanced ZKP-based messaging flows between
networks can be supported without compromising privacy.
Ecosystem Integration and Adoption
To ensure broad applicability and compatibility with EVM and non-EVM ecosystems, implementations of this specification MUST provide equivalent interfaces and functions that adhere to the described behavior and semantics.
While the exact syntax may differ depending on the specific programming language and runtime environment, the core functionality, input parameters, and return values SHOULD be analogous to those defined in the IDL interfaces within this specification.
This requirement allows developers to implement the crosschain interoperability protocols consistently across diverse DLT ecosystems, promoting seamless integration and interaction between different networks. By providing clear mappings and adaptations of the interfaces to their respective environments, platforms can ensure that the crosschain communication mechanisms operate predictably and reliably, regardless of the underlying technology stack.
Ethereum network
Using the crosschain messaging protocol described in this specification to facilitate interoperability with an Ethereum network is outlined in this section.
Crosschain Messaging Layer
Ethereum networks support block headers and event logs that can be used to implement event-based, state-based or transaction-based crosschain messaging by using block header proofs. This approach leverages the cryptographic security of the source network's consensus mechanism to establish the authenticity of crosschain messages. The resulting proof can be verified in an Ethereum smart contract once necessary setup has taken place.
Moreover, a trusted attestation layer verifying events, transactions or state changes can make use of, a less coupled proving scheme, where attestation signatures from trusted parties are used as verification mechanism.
The implementation of an crosschain connector contract, used for sending messages to an Ethereum network, and verifying proofs built around crosschain messages received from an Ethereum network, as described in this specification, is best explained (and maintained) when a separate connector contract is used for each remote Ethereum network.
Implementations of the interfaces defined in Section 3.3 (Crosschain Connector Interface) and Section 3.8 (Authentication Parameters) are required. A Solidity extract of the minimum messaging layer implementation is provided below.
contract CrosschainConnector is ICrosschainConnector {
// Section 3.3
function updateAndCommit(
uint256 networkId,
address contractAddress,
bytes calldata functionCallData
);
// Section 3.3: Equivalent, but returning specific parameters, to save on gas costs.
function decodeAndVerify(
uint256 networkId,
bytes calldata encodedInfo,
bytes calldata encodedProof
) returns (address contractAddress, bytes memory functionCallData);
// Section 3.8
function encodeAuthParams(
bytes calldata functionCallData,
uint256 networkId,
address callerAddress
) returns (bytes memory augmentedCallData);
// Section 3.8
function decodeAuthParams(
bytes calldata functionCallData
) returns (uint256 networkId, address callerAddress);
}
The CrosschainConnector contract performs the necessary state updates, when commiting to a crosschain message, targeted at another Ethereum network. It may emit an event, update a rolling hash or update an exit tree in storage. and performs proof verification before ex
Crosschain Function Call Layer
Implementation of the interface defined in Section 4.1 (Crosschain Function Call Interface) is required. A Solidity example of the minimum function call layer implementation is provided below.
contract InteropManager is ICrosschainFunctionCall {
function inboundCall(
uint256 networkId,
bytes calldata encodedInfo,
bytes calldata encodedProof
);
function outboundCall(
uint256 networkId,
address contractAddress,
bytes calldata functionCallData
);
}
To couple the messaging layer with the function call layer, implementations would typically identify the applicable connector contract based on the source (for inboundCall) or target (for outboundCall) network id, and use it to perform specific messaging layer functions for that network.
inboundCall: Invoke decodeAuthParams to authenticate and invoke decodeAndVerify to verify the inbound message.outboundCall: Invoke encodeAuthParams to append authentication parameters and invoke updateAndCommit to commit to an outbound message.
Corda network
Using the crosschain messaging protocol described in this specification to facilitate interoperability between a Corda network and an Ethereum network is outlined in this section.
Crosschain Messaging Layer
Corda does not have events in the same sense as Ethereum but a transaction attestation proof can be constructed instead and used in the transaction-based messaging mechanism outlined in section 3.6.3 (Transaction-based Attestation). Corda transactions are split up into component groups and their SHA-256 hashes are used as Merkle tree leaves in storage. The most important of these, for a Corda transaction attestation proof, are listed below:
- The outputs component group, containing the output data of the transaction.
- The commands component group, containing the commands that was executed during the execution of the transaction.
- The signers component group, containing the public keys of all participants that needs to sign the transaction.
- The notary component group, containing the public key of the notary that needs to sign the transaction.
The contents of the outputs and commands component groups is interpreted as an instruction and translated into an EVM function and corresponding function call parameters to facilitate a remote function call from a Corda network to an EVM-based network. Translation is done by registered parameter handlers for each function that is callable via the interop protocol.
Similar to the interop between two Ethereum networks, participant on-boarding will be required to provide sufficient security in a production environment. Even for EVM-based event attestation proofs, it might be necessary to maintain a list of active validators of the source network on the target network. For example, some QBFT network implementations using contract validator selection, no longer include the list of validator addresses in their block headers.
More generally, the network verifying a proof might need to maintain a list of authorized signatories in the verifying contract. Consensus on Corda transactions are reached among participants of the transaction and a notary, instead of a global network-wide validator pool. For this reason, it is necessary to verify that the signatures provided in the proof are from authorized signatories and match up with the required signers of the transaction as provided in the signers and notary component groups.
Corda signatures can use ECDSA with the SECP256K1 or SECP256R1 curve and SHA256 hashing, or EDDSA with the ED25519 curve and SHA512 hashing. Signatures are performed over a hash of the Merkle transaction tree root and metadata containing the signature scheme that was used. Proof and signature structures must use those defined in section 3.7.6 (Multivalued Merkle Inclusion Proofs).
The interface for encoding transaction data, for use in the transaction-based messaging mechanism, is given in section 3.6.2 (Transaction-based Interface). The structure of the transaction data (txData) is DLT specific and an example of a compliant Corda transaction attestation proof can make use of the following structures:
interface ICrosschainConnector {
typedef sequence<octet> bytes32;
typedef sequence<octet> bytes;
struct ComponentData {
uint8 groupIndex;
uint8 internalIndex;
bytes encodedBytes;
};
struct TxData {
bytes inputParameters;
string hashAlgorithm;
bytes32 privacySalt;
sequence<ComponentData> componentData;
};
};
Where the ComponentData structure contains Corda transaction component group data that needs to be decoded, hashed and checked for Merkle tree inclusion.
Properties:
groupIndex: Global transaction component group index.internalIndex: Internal component group index.encodedBytes: Contains a hex-encoded component group of the Corda transaction.
Where the TxData structure contains the Ethereum function input parameters, Corda component group data and algorithmic details to verify the component group hash's inclusion in the transaction tree.
Properties:
inputParameters: Input parameters to be verified as being included in the component data.hashAlgorithm: Hash algorithm used in the Merkle tree. Only SHA-256 is currently supported.privacySalt: Salt needed to compute a Merkle tree leaf.componentData: Hashes of these components become the values we want to proof Merkle tree membership of in our multivalued proof.
The encoded TxData struct is then included in the encodedInfo field as txData.
This multivalued Merkle inclusion proof can alternatively be turned in a zero-knowledge proof yielding a much lower EVM verification cost, with added privacy, but resource intensive proof generation.
The interface for the crosschain verifier contract on the EVM-based network, that is verifying the Corda proof, is outlined in section 3.3 (Crosschain verifier interface). To be able to fully integrate with an EVM network, a compliant Corda app would need to provide an equivalent implementation of decodeAndVerify to verify an EVM-based proof as listed in section 3.7 (Formats of Proofs). This evidently results in having to maintain an active list of EVM network validators, or authorised signatories, in the messaging layer of the Corda app.
Crosschain Function Call Layer
For every type of Corda transaction that gets added to the interop flows, and EVM function call instruction that can be created from it, a translator needs to be registered in the messaging layer. The translator consists of a mapping between Corda output component group data and EVM input function call parameters. The inputParameters in the TxData structure contains the call parameters of the function we want to call remotely through the function call layer.
Both the Corda app and the EVM contract MUST implement the interface in section 4.1.1 (Remote Function Call Interface), or an equivalent thereof, to allow functions to be called remotely on other networks.
It is worth noting that the Corda network, or the generator of the Corda proof, needs to know the destination EVM network identification and target contract address before invoking inboundCall on an EVM network. This information is not signed over as in the case of EVM event attestation, and care should be taken that the correct contract addresses are given to this layer.
The required authentication parameters in Section 3.8 (Authentication Parameters) contain an additional network identification number and contract address from where the event, transaction or state change originated. This, for EVM-based networks, provide the ability to verify the source network identification and contract address against the event, transaction or state data that was signed over in an attestation proof. The most obvious way to generalize this for Corda transaction attestation proofs, at the moment, is to use the Corda network parameters. For each contract class there is a list of SHA-256 hashes, of the approved Corda app jar versions containing the contract, that is included in the Corda network parameters as whitelisted contract implementations. A Corda transaction contains a SHA-256 hash of the source network parameters from where the transaction was sent which can be used in authorisation if we onboard and maintain the Corda network parameters on the EVM-based network.
Crosschain Application Layer
The application layer integration mainly consists of implementing Corda app and EVM smart contract flows involving specific functions that can be called remotely, via the crosschain function call layer. The underlying messaging protocol, which depends on the registered verification scheme in the crosschain messaging layer, translates a verifiable step (event, transaction or state change) in the flow, performed on a remote network, into a verified instruction that can be used to securely perform the next step in the flow on the local network. The application layer contains the business logic that gets invoked through the crosschain messaging protocol.
Any application layer implementation needs to also cater for unhappy paths in the flows to ensure assets don't get stuck without recovery. This is a requirement in any regulated financial environment. This involves cancellation of a flow, under special circumstances, to release assets by means of a remote function call and a cryptographic proof of a prerequisite step that occurred on a different network.
The existing use case using Corda and Ethereum focussed in on DvP (Delivery vs Payment) where securities reside on a Corda network and tokenized cash reside on an Ethereum network in deposit token contracts. The crosschain messaging protocol is used to facilitate remote crosschain function calls between the two ledgers, and an execution plan, involving fixed flows, was build on top of the protocol to do intraday repo trades. The approach followed a standard hold to execute approach where assets and cash are placed on hold and holds are executed after verification of proof that either the hold was placed on the other network or the hold was executed on the other network.
Algorand network
Using the crosschain messaging protocol described in this specification to facilitate interoperability between an Algorand network and an EVM-based network is outlined in this section.
Crosschain Messaging Layer
For Algorand to be compatible with the crosschain messaging protocol discussed in this document, it must support an event, transaction or state attestation proof as specified in section 3.7.
An Algorand block contains a transaction root, which authenticates the set of transactions appearing in the block, as the root of a Merkle tree with transaction ids as leaves, in lexicographic order. This can naturally be turned into a transaction attestation proof
An Algorand state proof is a cryptographic proof of state changes that occur in a given set of blocks. State proofs are created and signed by the Algorand network itself, so they can be used to verify that a state change happened on the Algorand network. State proofs use quantum-safe Falcon keys. An EVM pre-compile for verification of this signature scheme was proposed in EIP 7592 but these signature are not currently supported.
Algorand make use of events as part of log functions. Since Algorand supports structured logging via the log primitive and the ARC‑28 event format, an event payload, including fields such as destination network id, target contract address, and function call data, can be used.
Algorand uses ED25519 signature scheme for authorization and uses SHA-512/256 hash function for creating contract account addresses from TEAL bytecode. It is recommended to support ECDSA using the SECP256K1 curve and KECCAK-256 hashing algorithm for better verification times in the EVM.
Messaging components MUST support an equivalent interface as described in section 3.3 (Crosschain Connector Interface).
On Algorand chain
def decodeAndVerify(networkId:abi.uint256, encodedInfo: abi.byte[], encodedProof:abi.byte[], output:abi.byte[] )-> Expr: return output.set(decodedInfo)
The definition of networkId, encodedInfo and encodedProof are similar to the EVM definition.
To perform encoding for message info, the encoded rules of Algorand specification (https://github.com/algorandfoundation/ARCs/blob/main/ARCs/arc-0004.md) should be used.
Crosschain Function Call Layer
Algorand should support compatible remote function call libraries to initiate a remote function call to another network and execute a remote function call locally after verifying a proof from another network as described in Section 4.1 (Corsschain Function Call Interface).
On the Algorand chain, this remote function call can be defined as
def outboundCall(networkId:abi.uint256, contractAddress: abi.address, functionCallData:abi.byte[] )-> Expr
def inboundCall(networkId:abi.uint256, encodedInfo: abi.byte[], encodedProof:abi.byte[] )-> Expr
def CrosschainFunctionCall(networkId:abi.uint256, contractAddress: abi.address, functionCallData:abi.byte[] )-> Expr
Stellar (Soroban) network
Using the crosschain messaging protocol described in this specification to facilitate interoperability between a Stellar (Soroban) network and an EVM-based network is outlined in this section.
Crosschain Messaging Layer
For Stellar(Soroban) to be compatible with the crosschain messaging protocol discussed in this document, it must support an event, transaction or state attestation proof as specified in section 3.7.
Stellar(Soroban) make use of events as part of env struct, which can be used in the crosschain message protocol described in this document.
Messaging components MUST support an equivalent interface as described in section 3.3 (Crosschain verifier interface).
This function could be:
pub struct Signature {
by : BytesN<32>,
sig_r: U256,
sig_s: U256,
sig_v: U256,
meta: BytesN<32>
}
pub struct Proof {
typ: U256,
proof_data: Bytes,
signatures: Vec,
}
trait ICrosschainConnector {
fn decode_and_verify(network_id: U256, encoded_info: Bytes, encoded_proof: Bytes) -> Bytes;
fn update_and_commit(networkId: U256, contractAddress: BytesN32, functionCallData:Bytes) -> Bytes;
}
The definition of networkId, encoded_info and encoded_proof are similar to the EVM definition.
Crosschain Function Call Layer
Stellar(Soroban) should support compatible remote function call libraries to initiate a remote function call to another network and execute a remote function call locally after verifying a proof from another network as described in section 4.1.1 (Remote Function Call Interface).
On the Stellar(Soroban) chain, this remote function call can be defined as
pub fn inbound_call(env: Env,
network_id: U256, //stellar chainid
encoded_info: Bytes,
encoded_proof: Bytes,
)
fn outbound_call(env: Env, network_id: U256,target_contract_address: Bytes, function_calldata: Bytes,source_contract_address: Address );
Cosmos network
Using the cross-chain messaging protocol described in this specification to facilitate interoperability between a Cosmos network and an EVM-based network is outlined in this section; however, it does not define specific requirements for an EVM network to verify Cosmos proofs.
Crosschain Messaging Layer
The Cosmos ecosystem has a built-in Inter-Blockchain Communication (IBC) mechanism that provides a communication framework based on Light Client Verification. Specifically, IBC includes specifications for Light Clients (ICS-2), primitive communication constructs such as Connections (ICS-3), Channels/Packets (ICS-4), and the underlying Commitments (ICS-23). Full details of the protocol can be found in ICS.
Light Client in IBC
In the IBC framework, a Light Client plays a crucial role:
- It tracks the consensus state and proof specifications of the counterparty chain.
- It holds commitments necessary for verifying messages from the counterparty chain.
In the ICS framework, verification is divided into two main steps: 1) updateClient and 2) verifyMembership.
updateClient
updateClient is the function for updating the consensus state of the counterparty chain. While the specification is broadly defined, it can be implemented as a procedure to update from an old consensus state to a new height and new consensus state by vefifying a Header:
updateClient = {header: Header, prevConsensusState: ConsensusState} -> (NewHeight, ConsensusState)
Where ConsensusState = (root: CommitmentRoot, timestamp: uint64)
For more details on implementation, refer to Handling Client Messages in IBC.
verifyMembership
verifyMembership uses the consensus state to perform state verification. Implementations may include Merkle proof verification using accepted StateRoot. For more information on implementation, see Packet Commitment Verification in IBC.
Mapping to EEA Specification
The EEA's Crosschain Messaging Layer specification can be considered as defining the verifyMembership step. Specifically:
encodedProof can be viewed as an Ethereum ABI-encoded CommitmentProof as defined in ICS-23.encodedInfo can be considered as the encoding of the new consensus state obtained from updateClient, along with CommitmentRoot, CommitmentPath, and Value.- The
decodeAndVerify function can be seen as decoding these elements and internally executing verifyMembership = (root: CommitmentRoot, proof: CommitmentProof, path: CommitmentPath, value: Value) => boolean to perform state verification.
It is worth noting that the updateClient step in ICS specifies a mechanism for verifying and accepting Header. When verifying multiple Key-Value pairs against a single Header, it is beneficial from a processing efficiency standpoint to have these as separate primitives.
Implementation Considerations
For implementations seeking to align with ICS and fully integrate with the Cosmos network, ibc-solidity provides an EVM-compatible implementation of ICS components, including updateClient and verifyMembership.
FinP2P network
Using the crosschain messaging protocol described in this specification to facilitate interoperability between an arbitrary DLT network, connected to the FinP2P network, and an Ethereum network is outlined in this section.
The FinP2P system uses routers, which serve as a connection point between different participants involved in the DLT ecosystem of tokenized assets. These routers utilize the open FinP2P protocol to unify user identities, wallets, data structures, messaging and orchestration of DLT transactions. They can be used as a network of trusted peers, signing receipts, to attest to finalized transactions on the underlying DLT networks they are connected to.
FinP2P receipts, when part of an execution plan, can be used to enable interoperability between two of the underlying DLT networks, by trusting router signatures over FinP2P receipts. This allows for a mode of interoperability where the heterogeneous DLT networks are less coupled. That is, the verifying DLT network doesn't need to understand the workings of the DLT network where the transaction originated. This means that EVM verifiers can be standardised around processing generic FinP2P receipts and verifying the signatures over them. This comes at the cost of an additional layer of trusted peers instead of relying on the consensus participants of the underlying DLT network.
The FinP2P network can also facilitate interoperability between two DLT networks by routing around ledger specific proofs, as part of the receipt, as is described in section 3.7 of this document. Verifier contracts handling such proofs will do so independently of whether the proofs were routed via FinP2P or not.
The FinP2P open source specifications are available here.
Crosschain Messaging Layer
A signed FinP2P receipt is encoded, hashed and signed using EIP712. Using a known Receipt structure allows the EVM verifier to extract data from the encoded structure and translate it into a command and EVM smart contract function call parameters. FinP2P receipts are defined below:
{
"types": {
"EIP712Domain": [
{"name": "name", "type": "string"},
{"name": "version", "type": "string"},
{"name": "chainId", "type": "uint256"},
{"name": "verifyingContract", "type": "string"}
],
"Account": [
{"name": "accountType", "type": "string"},
{"name": "finId", "type": "string"}
],
"TransactionDetails": [
{"name": "operationId", "type": "string"},
{"name": "operationType", "type": "string"},
{"name": "transactionId", "type": "string"}
],
"Asset": [
{"name": "assetId", "type": "string"},
{"name": "assetType", "type": "string"}
],
"TradeDetails": [
{"name": "executionPlanId", "type": "string"},
{"name": "instructionSequenceNumber", "type": "string"}
],
"Receipt": [
{"name": "id", "type": "string"},
{"name": "source", "type": "Account"},
{"name": "destination", "type": "Account"},
{"name": "asset", "type": "Asset"},
{"name": "tradeDetails", "type": "TradeDetails"},
{"name": "transactionDetails", "type": "TransactionDetails"}
]
}
}
Supported FinP2P signatures use ECDSA with the SECP256K1 curve and KECCAK hashing for optimized verification in the EVM. Signatures are encoded according to the EEA specification as defined in section 3.7.1 (Multiple ECDSA Signatures) to hold FinP2P receipt signatures.
The interface for encoding transaction data, for use in the transaction-based messaging mechanism, is given in section 3.6.2 (Transaction-based Interface). The structure of the transaction data (txData) is DLT specific and an example of a compliant FinP2P transaction attestation proof can make use of the following structures containing a FinP2P receipt:
struct EIP712Domain {
string name;
string version;
uint256 chainId;
address verifyingContract;
}
struct Asset {
string assetId;
string assetType;
}
struct TransactionDetails {
string operationId;
string operationType;
string transactionId;
}
struct TradeDetails {
string executionPlanId;
uint256 instructionSequenceNumber;
}
struct Account {
string accountType;
string finId;
}
struct Receipt {
string id;
Account source;
Account destination;
Asset asset;
TradeDetails tradeDetails;
TransactionDetails transactionDetails;
}
struct TxData {
bytes inputParameters;
string command;
EIP712.EIP712Domain domainParameters;
Receipt receipt;
}
Where the EIP712Domain structure contains FinP2P domain parameters.
Properties:
name: The user readable name of the signing domain.version: Current major version of the signing domain.chainId: The EIP-155 chain id.verifyingContract: Destination verifying contract address.
Where the Receipt structure contains FinP2P receipt data.
Properties:
assetId: Asset identification, e.g. ownera, USD, BTC.assetType: Asset type, e.g. finp2p, fiat, cryptocurrency.operationId: Operation identification on the FinP2P network.operationType: Type of operation performed by the transaction.transactionId: Transaction identification on the underlying DLT network.executionPlanId: Execution plan identification corresponding to a unique trade identifier.instructionSequenceNumber: Unique instruction number for the step of the execution plan that was performed.accountType: Type of FinP2P account, e.g. finp2pfinId: FinP2P account identification in the form of a compressed public key.id: Unique receipt identification.source: Source FinP2P account.destination: Destination FinP2P account.asset: Asset used in the trade.tradeDetails: Trade details.transactionDetails: Transaction details.
Where the TxData structure contains the Ethereum function input parameters, FinP2P receipt data and domain parameters required to recreate the hash that was signed.
Properties:
inputParameters: Input parameters to be verified as being included in the receipt data.command: The unique command constructed from the receipt contents that is used to make the remote function call.domainParameters: EIP712 domain parameters needed to encode typed data.receipt: The FinP2P receipt.
The ABI-encoded TxData struct is then included in the encodedInfo field as txData.
The interface for the crosschain verifier contract on the EVM-based network, that is verifying the FinP2P receipt proof, is outlined in section 3.3 (Crosschain verifier interface).
Crosschain Function Call Layer
For every FinP2P receipt, pertaining to a specific execution plan instruction, that gets added to the interop flows, and EVM function call that can be created from it, a translator needs to be registered in the messaging layer. The translator consists of a mapping between receipt fields and EVM input function call parameters. The inputParameters in the TxData structure contains the call parameters of the function we want to call remotely through the function call layer.
EVM and non-EVM based DLT networks MUST implement the interface in section 4.1.1 (Remote Function Call Interface), or an equivalent thereof, to allow functions to be called remotely with a proof that a previous step in the execution plan was executed successfully.
The FinP2P adapter that generates the proof from the receipt needs to know the target network information, where the receipt will be verified, as well as the target contract address where the remote function call must be executed. This information is included in encodedInfo when invoking inboundCall on an EVM network. It is not signed over as in the case of EVM event attestation, and care should be taken that the correct contract addresses are given to this layer.
Crosschain Application Layer
The application layer integration consists of implementing specific functions that can be called remotely, via the crosschain function call layer. The existing use case using FinP2P with Ethereum focussed in on DvP (Delivery vs Payment) where securities reside on the FinP2P network as tokenized assets and tokenized cash resides on an Ethereum network in deposit token contracts. The crosschain messaging protocol is used to facilitate remote crosschain function calls to transfer the asset in the FinP2P network and provide payment for it on Ethereum. The approach makes use of FinP2P escrow services to hold and transfer assets. Holds are executed after verification of proof that either the hold was placed on the other network or the hold was executed on the other network.
Considerations
Interoperation Modes
The ISO Blockchain and Distributed Ledger Technology — Interoperability Framework (ISO/CD TS 23516) identifies three interoperation modes: Data Transfer, Asset Transfer, and Asset Exchange. Data Transfer involves copying information between DLTs, potentially with intermediate processing. Asset Transfer allows for the movement of assets from one DLT to another, often involving locking or burning the original asset and creating a wrapped token on the destination network. Asset Exchange enables atomic swaps of assets between different DLTs, where participants must be present on both networks, and the assets remain on their native chains while changing ownership addresses.
Smart Contract Upgradability
Smart contract upgradability a critical aspect to consider in the development of a DLT interoperability implementation, particularly for long-term viability and compliance with evolving regulatory standards. Smart contracts, once deployed, are immutable on the ledger. However, financial regulations and business logic may evolve, necessitating updates to the contracts. Implementing upgradable smart contracts through proxy patterns or versioning systems allows for the modification of contract logic without changing the contract's address or deployed bytecode. This approach must be carefully designed to maintain the integrity and security of the contracts, especially in a regulated financial context. Upgradability mechanisms should include strong governance processes to control updates and prevent unauthorized changes. Additionally, considering the crosschain interoperability, the upgradability strategy should ensure consistency and compatibility across different DLT platforms, enabling seamless interaction and compliance with regulatory changes over time.
Data Type Convertibility and Compatibility
Interfaces defined in this specification should convert effortlessly to languages like Solidity, Python and Rust as long as the types defined in the IDL interfaces are properly mapped in the conversion code.
It is important to note that certain data types, such as uint256 and bytes32, are used as distinct types in interfaces but can readily be transformed from one into the other through simple data format conversions.
It is recommended that smart contracts and off-chain relays support all the defined data types to enhance interoperability and flexibility in data handling across different DLT platforms. Developers should ensure that their implementations incorporate mechanisms for the straightforward conversion between these data types, where necessary, to maintain the integrity and fidelity of data as it moves across network boundaries.